Secure Compute
Secure Compute is available for purchase on Enterprise plans
Secure Compute creates private connections between your Vercel Functions and your backend infrastructure like databases, APIs, or any private services you're running.
By default, Vercel deployments can come from any IP address. Secure Compute gives you dedicated static IPs, so you can tighten your backend's access controls to only allow traffic from your specific Vercel infrastructure.
When you enable Secure Compute on your project, your deployments and build container get their own dedicated network with static IP addresses in a region you choose. Your traffic stays completely separate from other customers.
You can provision and manage your own Secure Compute networks directly from the Vercel dashboard. Create networks for different teams, projects, or environments, all through self-service.
If you only need static IP addresses for IP allowlisting, without features like dedicated infrastructure, VPC peering, or complete network isolation, consider Static IPs.
Here's what you get with Secure Compute:
- Your own dedicated private network inside a VPC
- Static IPs that won't change, plus a NAT Gateway
- Complete isolation — only your specified resources can reach your Vercel Functions
You can create Secure Compute networks directly from the Vercel dashboard:
- Navigate to your team's Settings → Connectivity.
- Click Create Network to start the setup process.
- Select your desired Region: choose the region closest to your backend infrastructure for best performance.
- Optionally expand Advanced options to configure:
- CIDR Address Block: Specify a custom private IPv4 address range.
- Availability Zones: Select specific AWS Availability Zones within your chosen region.
- Click Next to review your settings.
- Click Create Network to provision your network.
Once created, your network includes:
- A pair of dedicated IP addresses
- AWS account ID
- AWS region based on your selection
- AWS VPC ID
- CIDR block based on your selection
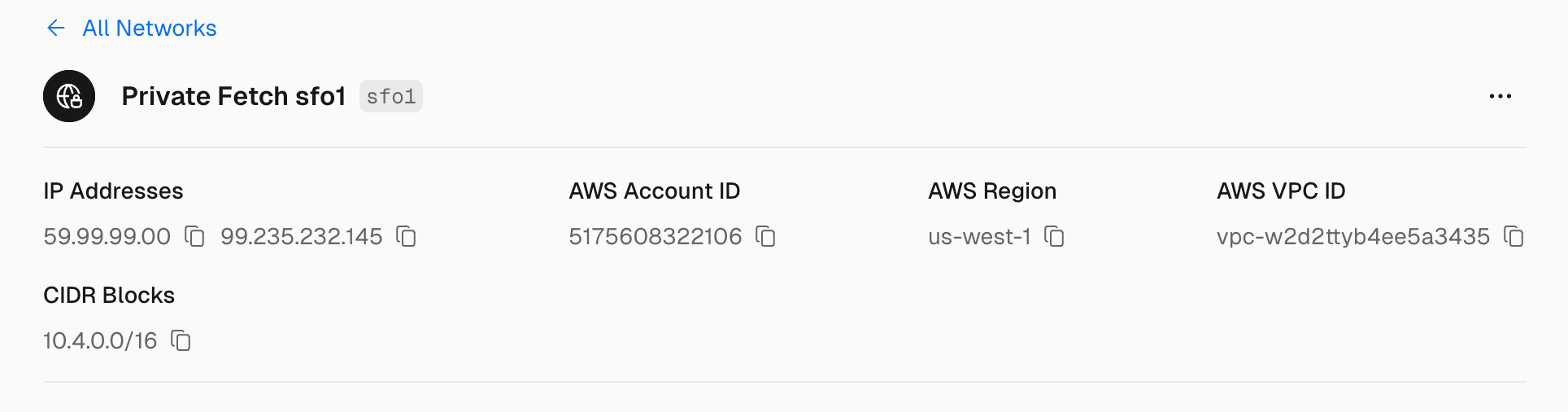
When you enable Secure Compute on a project, Vercel attaches your project's build container and subsequent deployment inside a Secure Compute network with a specific IP address pair (dedicated IP). You can choose to exclude the build container from the private network.
Each private network has its own dedicated IP pair and is isolated from others, ensuring no sharing across teams. You can assign multiple projects to a Secure Compute network, but each project belongs to only one active and one passive network.
You can create multiple Secure Compute networks for your team directly from the dashboard. For example, separate networks for different projects, environments, or teams. Navigate to your team's Settings → Connectivity and click Create Network to add additional networks.
Once your IP pair is ready, add it to your backend's access control list. You'll still need to use a username/password or authentication key on top of the IP filtering — the IPs alone aren't enough.
When you create a Secure Compute network, you select the Vercel Function region where it will be provisioned. For the best performance, pick the same region where your backend runs.
Vercel applies Secure Compute to Vercel Functions using the following runtimes:
The Edge Runtime is not supported meaning features like Routing Middleware and Vercel Functions using the edge runtime will not use the provided dedicated IP addresses.
Secure Compute supports automatic region failover using the active and passive network concept. Each project environment can have:
- Active Network: The primary Secure Compute network where your functions run
- Passive Network: A secondary network in a different region for automatic failover
To set up region failover:
- Create networks in different regions: Navigate to your team's Settings → Connectivity and click Create Network to create Secure Compute networks in your primary and failover regions.
- Connect project environments: In your project's Settings → Connectivity, configure each environment (Production, Preview, etc.) with an Active Network (primary) and an optional Passive Network (failover).
- Automatic failover: When enabled, Vercel automatically switches to the passive network if the primary region becomes unavailable, ensuring your Vercel Functions continue to operate.
To add a project to your Secure Compute network:
- Navigate to your project's Settings → Connectivity.
- For every environment you want to connect to Secure Compute:
- Select an Active Network.
- Optionally select a Passive Network to enable passive failover.
- Optionally enable Builds to include the project's build container in the network.
- Click Save to persist your changes.
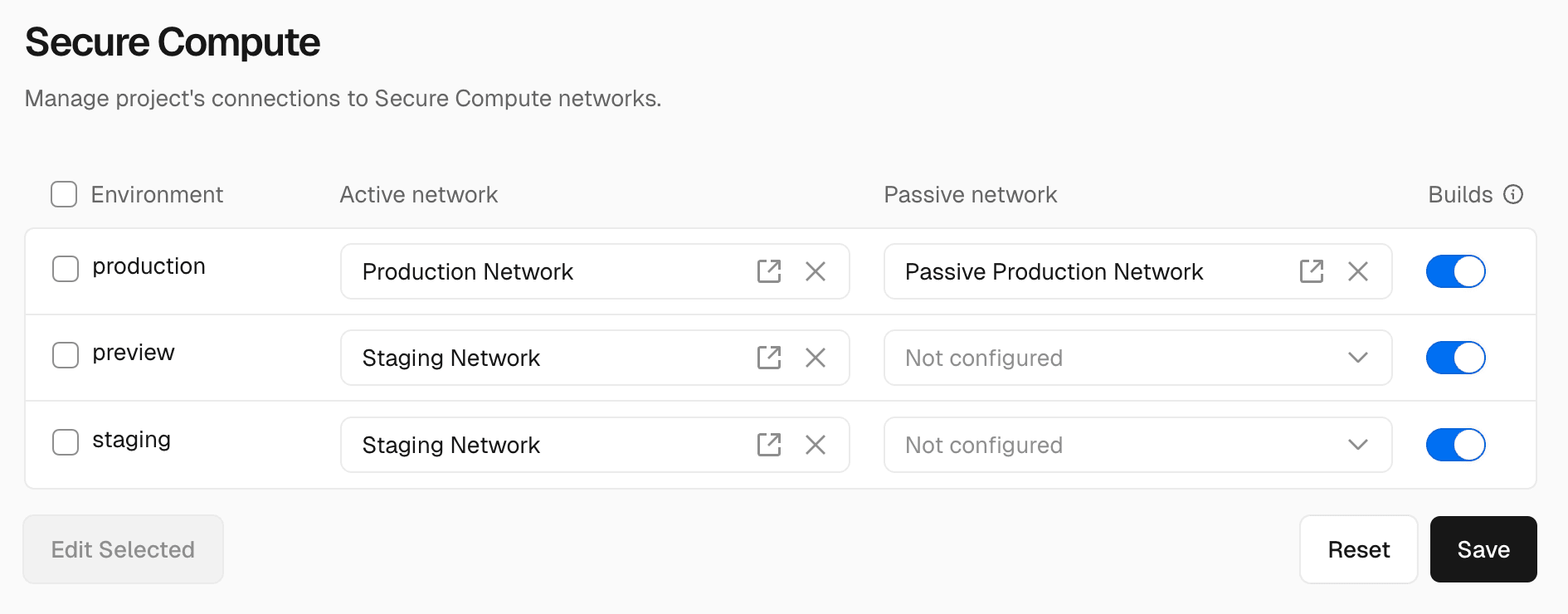
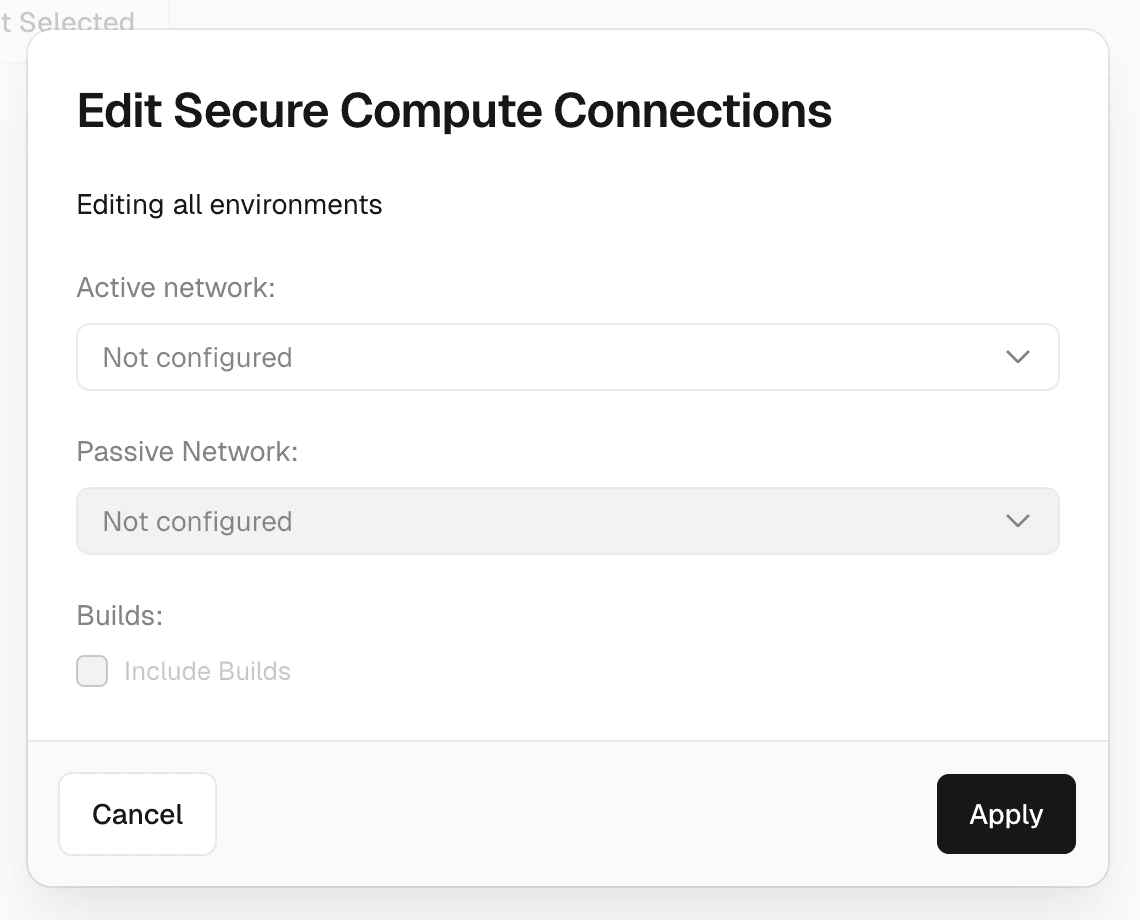
To change multiple environments at once:
- Select the environments using checkboxes or use the checkbox in the table header to select all environments.
- Click Edit Selected.
- In bulk edit modal:
- Select an Active Network.
- Optionally select a Passive Network to enable passive failover.
- Optionally check Include Builds to include the project's build container in the network.
- Click Apply to modify the selected environments.
- Click Save to persist your changes.
When you add a project to a Secure Compute network, you can choose to include the project's build container in the network. This is useful if your application calls your data sources at build time.
You can opt the build container out of using the dedicated IP addresses. This is useful if your application only calls your data sources at run time and not at build time.
By opting out of including the build container, you will not incur the 5s delay when provisioning a secure build container.
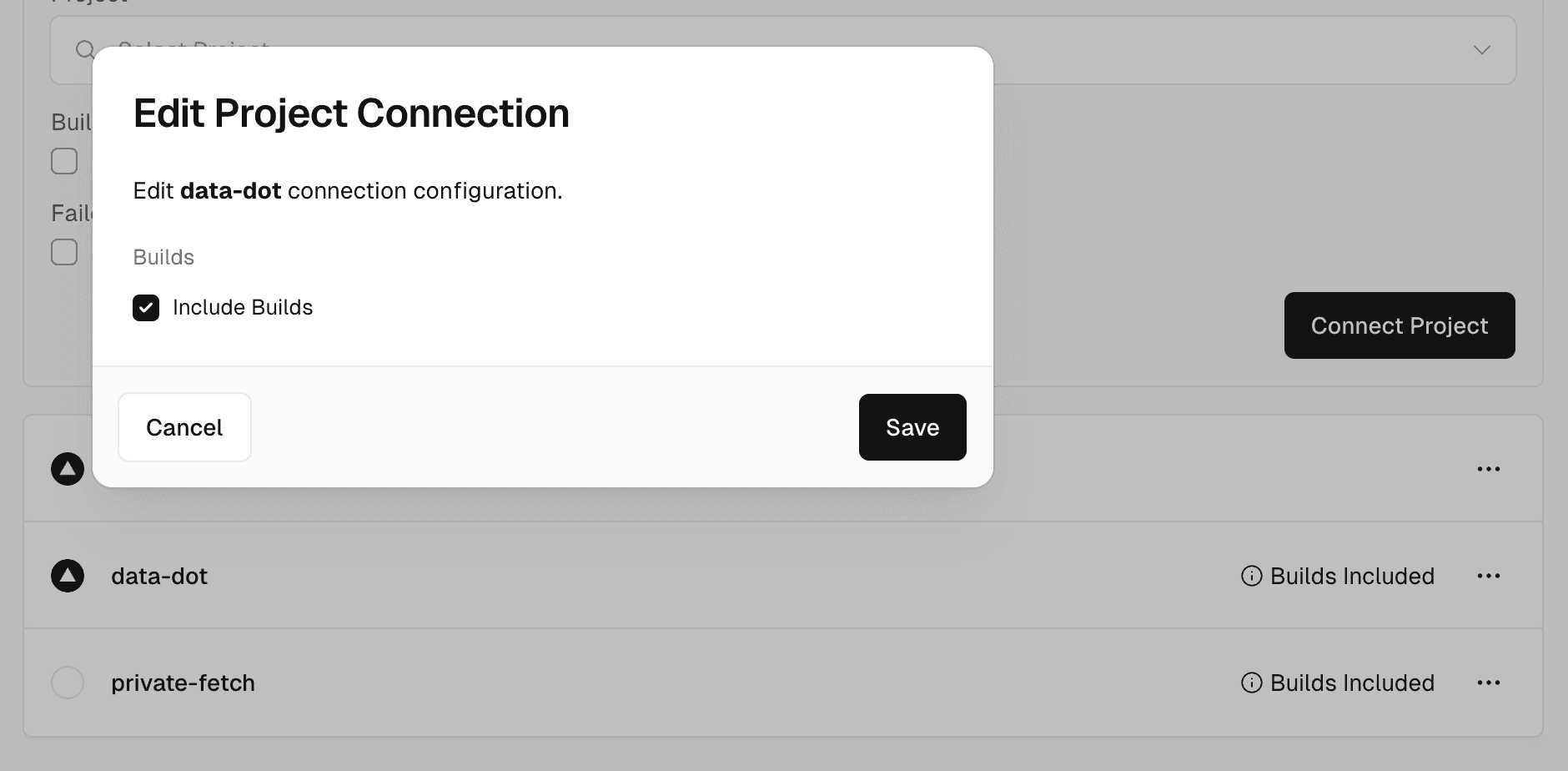
To manage the build container during the project connection process select Include Builds.
To manage the build container after the project is connected to the Secure Compute network:
- Navigate to your team's Settings → Connectivity.
- Select a private network from the list.
- Select the Projects tab.
- Click the icon to the right of your connected project and click Edit.
- Check/uncheck Include Builds to include/exclude the project's build container in the network.
- Click Save.
You can use one network with multiple projects in the same team. In this case, the same IP pair is shared across multiple projects.
If you require additional security or have a large team, you can have one network for each project so that each project will have its own dedicated IP pair.
Connecting a project to multiple networks across different regions is currently not supported. Each project environment can only be linked to a single active network within a single region. A passive network in a different region may only be used for failover.
Virtual private cloud (VPC) peering is a method of connecting two VPCs in the same or different region. When you use Secure Compute, Vercel accepts a VPC peering connection between your Vercel Secure Compute network and your AWS VPC.
To set up VPC peering:
- Create a Secure Compute network: Navigate to your team's Settings → Connectivity and click Create Network. Select your desired region and optionally specify a CIDR block. The CIDR blocks of your Secure Compute network and your AWS VPC must not overlap.
- Set up peering in AWS: In your AWS VPC dashboard, configure the peering connection by copying the values from your Secure Compute network settings, and pasting in the AWS VPC peering connection settings:
- Requester VPC ID: Your VPC ID
- Account ID: The AWS account ID
- Accepter VPC ID: Your Vercel Secure Compute network's VPC Peering ID
- Region: Your Vercel Secure Compute network's region
- Create peering connection: In the AWS VPC peering connection settings, click Create Peering Connection to establish the connection.
- Accept peering connection: Go back to your Vercel dashboard and click Accept to accept the connection.
- Update route tables: Go to AWS's VPC dashboard, select Route Tables, and configure routing to allow traffic from Vercel's CIDR block.
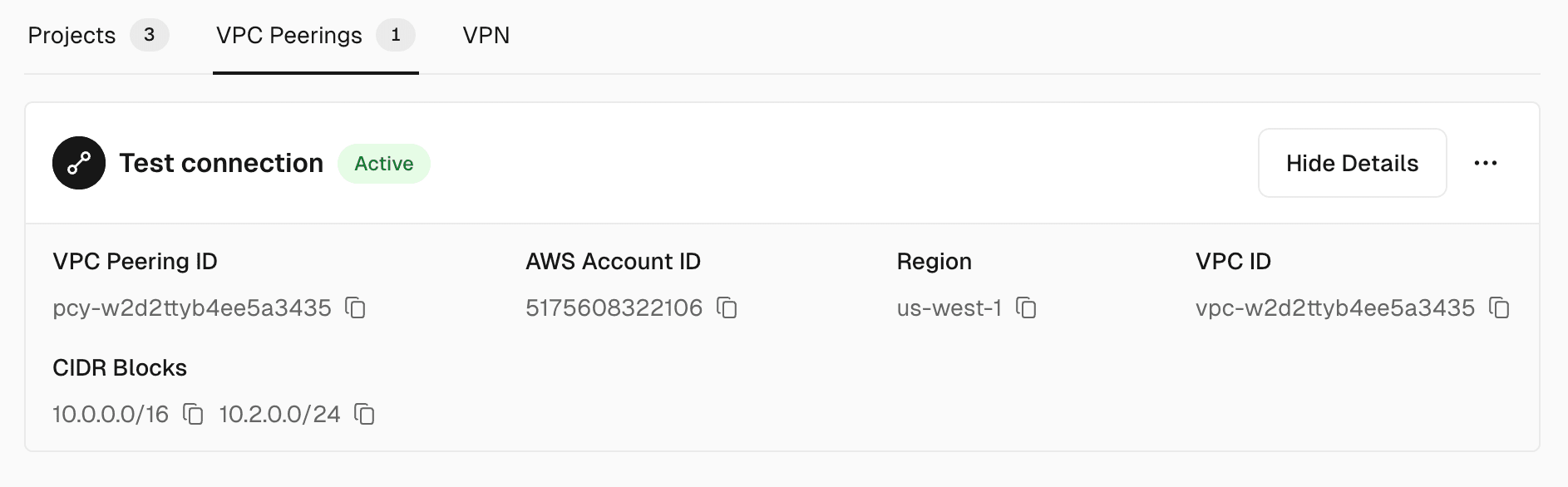
The connection can be deleted from either the Vercel dashboard, or the AWS VPC dashboard.
If your current security and compliance obligations require more than dedicated IP addresses, contact us for guidance related to your specific needs.
Secure Compute starts at $6.5K/year for Enterprise teams, plus Secure Connect Data Transfer at $0.15/GB.
Data transfer costs apply to all outbound traffic from your Vercel Functions to external services:
- Database queries and responses
- API calls to third-party services
- File uploads and downloads
- Any other outbound network traffic
Monitor your usage in the Team Settings Usage tab under the Secure Connect Data Transfer section.
When connected to a Secure Compute network, builds experience up to a 5s delay as they provision a secure build container. When this happens, your build is marked as Provisioning Container in the dashboard.
The maximum number of VPC peering connections that can be established per network is 50.
Was this helpful?

