Using reverse proxies like Cloudflare will limit Vercel's traffic visibility for security measures, introduce latency that degrades performance, and create cache management issues that may affect reliability. We do not recommend using a reverse proxy in front of Vercel.
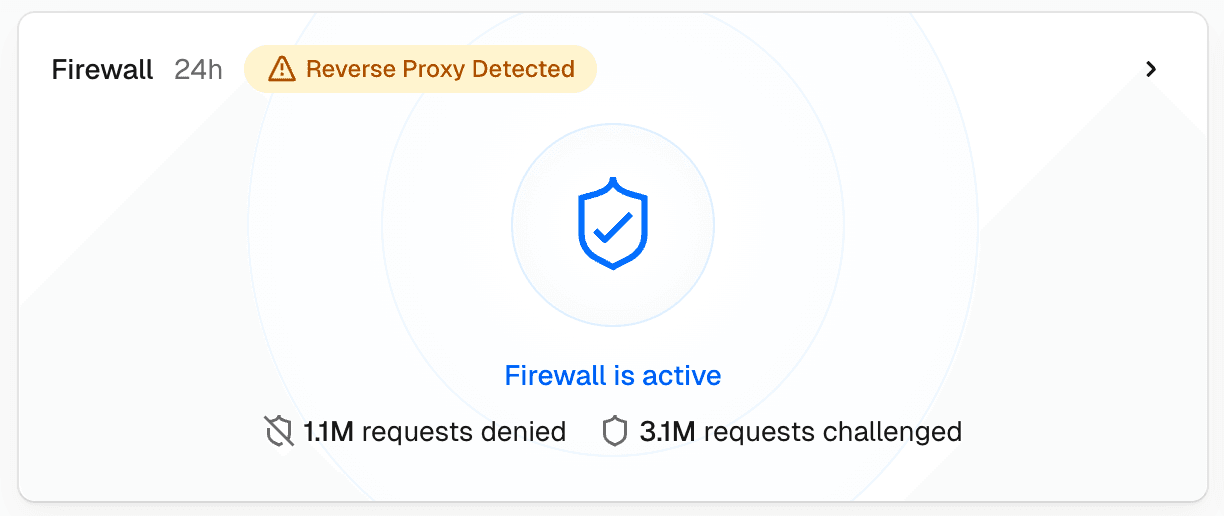
We recommend moving to Vercel as your DNS provider. Learn more.
We discourage using reverse proxies (e.g. Cloudflare, Azure, or other CDNs) in front of Vercel when Bot Protection is enabled. This setup significantly degrades detection accuracy and performance, resulting in a poor end-user experience.
Reverse proxies interfere with Vercel's ability to reliably identify bots:
- Obscured detection signals – Legitimate users may be incorrectly challenged because the proxy masks signals that Bot Protection relies on.
- Frequent re-challenges – Some proxies rotate their exit node IPs frequently, forcing Vercel to re-initiate the challenge on every IP change.
Vercel offers native support for using a reverse proxy through rewrites and our Edge Network is both a Content Delivery Network (CDN) and a globally distributed platform for running compute in regions around the globe.
While it is possible to stack an external proxy or load balancer in front of Vercel, we do not recommend this approach. The biggest disadvantage is that Vercel no longer has full traffic visibility, which prevents the Vercel Firewall and our threat intelligence products from working to their full potential. This includes our ability to automatically challenge requests, prevent DDoS attacks, and more.
Learn more about reverse proxies with Vercel.
Vercel offers native support for wildcard domains.
Enterprise plan customers can issue a Cloudflare Origin CA certificate with a wildcard SAN (Subject Alternative Name) and upload it on Vercel, if required to use Cloudflare.

